Call our toll free concierge service to help you 888-894-5573
FEATURED IN






Need help finding the best service for you?
Get help finding tv & internet in your area with our free concierge service. Our experts will also help you find savings with your local providers.
Call 7 days a week | 8:00am - 6:00pm PST:
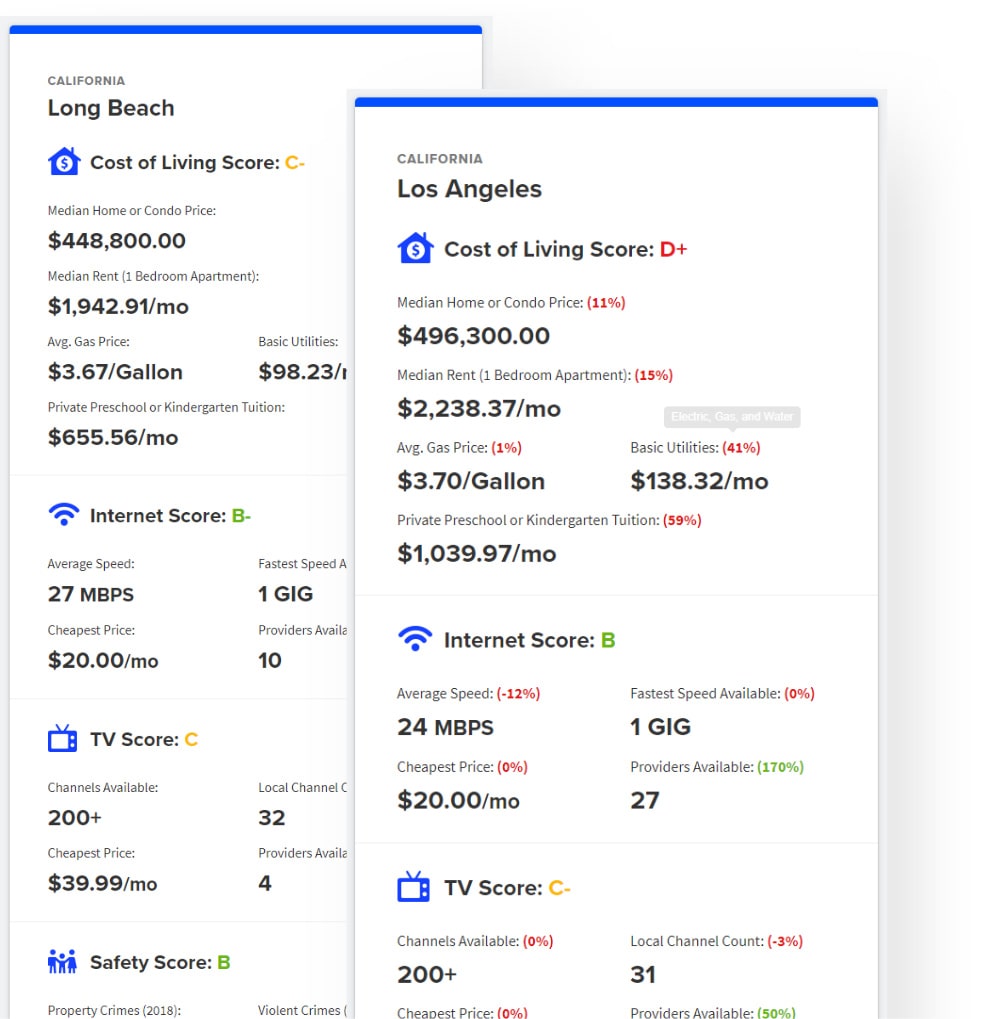
Moving?
Try our calculator.
Compare the cost of moving, home service availability, and safety between two cities
Need Help Getting Started?
Want to learn a little more before your call? Our buying guides can help you understand what service fits your needs best.

Military Buying Guide
Check out our buying guides to help you choose the best internet and tv provider for your budget & needs
Let's get you connected.
Find every broadband internet, TV, & utility provider's plans and pricing with a simple address.